Student researchers seek to improve cybersecurity of vehicle-to-vehicle communications
Team develops security features testbed and visual interface for V2V technology research
A team of RIT cybersecurity student researchers is working to make vehicle-to-vehicle communications more secure, so the technology can be implemented and help save lives.
If cars talked to each other, it would improve the travel experience and help save lives—but it could also lead to malicious, even life-threatening, cyberattacks. As a result, most car manufacturers have been hesitant to deploy vehicle-to-vehicle (V2V) communications technology.
At Rochester Institute of Technology, a team of student researchers are working to bridge this cybersecurity gap in V2V communications. The researchers hope their work can be used to help roll out V2V technology in a safe and secure way, as soon as possible — and eventually for use in self-driving cars.
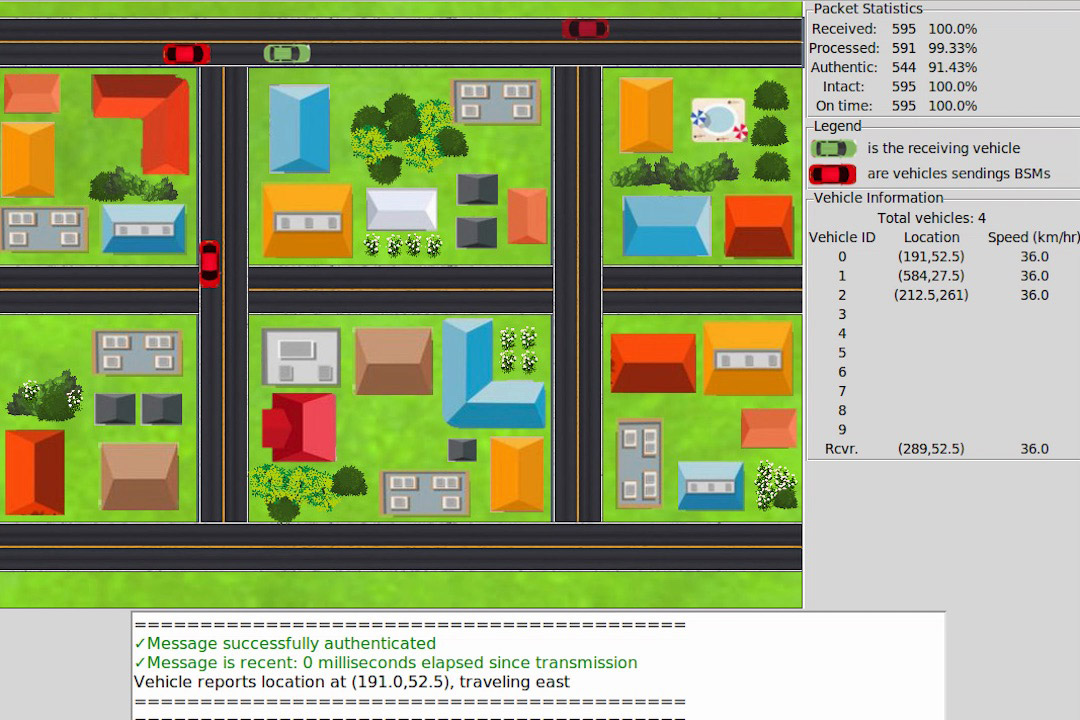
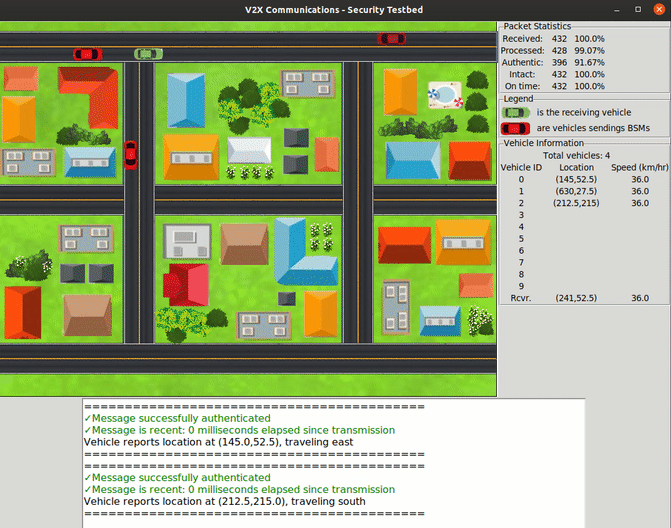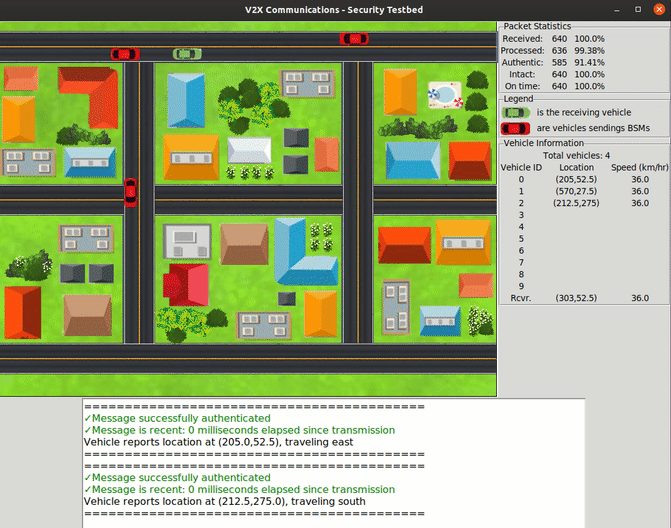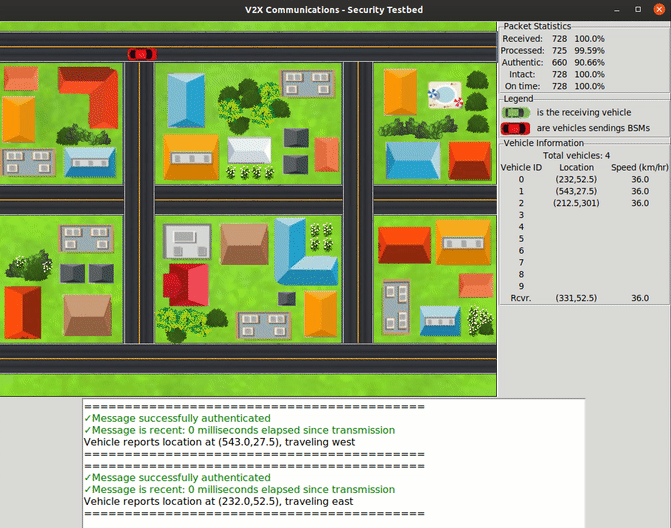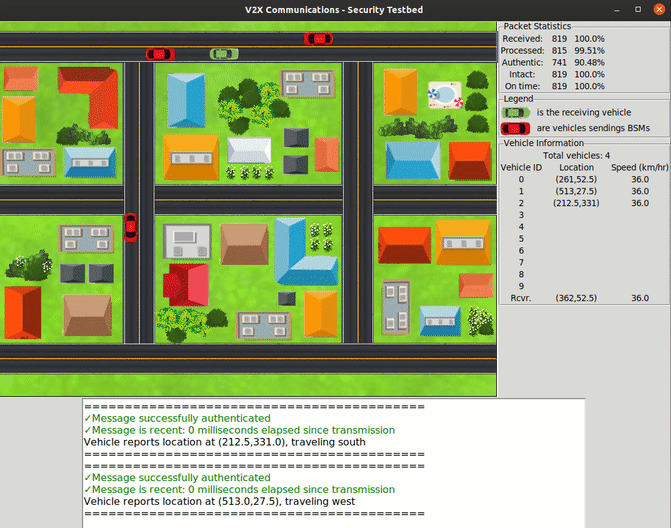
For the project, students have created a prototype of secure V2V communications that uses software-defined radios to represent vehicles that can exchange messages. The team implemented IEEE industry standards for integrity verification and vehicle authentication to ensure that those messages are legitimate and tamper-resistant, while preserving privacy. They also designed and built a visual interface that renders these communications in real time, allowing researchers to track the actions that each vehicle makes in a simulated scenario.
Student team's prototype of secure V2V communications system.
According to the U.S. Department of Transportation, V2V communications could prevent about 600,000 vehicle collisions and save 1,080 lives every year. However, the technology is more than a decade old and it hasn’t been deployed at a large scale due to security and safety concerns.
“There are significant security problems that could actually make V2V-equipped vehicles more dangerous than current models,” said Geoff Twardokus, a fifth-year computing security BS/MS student from Ithaca, N.Y. “For example, if there is no way to verify who is sending messages, what stops someone with bad intentions from abusing this technology to cause a collision, rather than avoid one?”
As part of a capstone project, the undergraduate students sought to create a wireless testbed that future research teams can use to investigate secure V2V communications. The student team includes Twardokus and 2020 computing security graduates Samantha Baker, who is from San Francisco; Peter Carenzo, who is from Hatboro, Pa.; Jaime Ponicki, who is from Clarence, N.Y.; and Aashish Annarapu, who is from India. The class was led by Hanif Rahbari, assistant professor in RIT’s Department of Computing Security.
The team used two Universal Software Radio Peripherals (USRPs) — programmable communication devices that are controlled by software — to emulate two vehicles that can wirelessly talk with each other. In order to make the communications secure, the team developed code to add security mechanisms based on the IEEE 1609.2 standard for securing V2V communications.
“The authentication mechanism we implemented uses digital signatures to validate the integrity and source of every V2V communication,” said Twardokus. “Essentially, through the use of cryptography, whenever a vehicle receives a message it can mathematically verify that the message is fresh and intact (the message received is identical to the message as it was originally sent). Also, that the message was definitely sent by a vehicle that is considered legitimate by the transportation system.”
In the absence of this security protocol, attackers could spoof critical safety messages to misguide vehicles and jeopardize passenger’s lives, time and assets, explained Rahbari.
“The protocol itself already exists, but to the best of my knowledge, it has not previously been incorporated into real wireless communications in an open-source USRP-based testbed for research and evaluation,” said Rahbari. “The industry is currently not convinced that 1609.2 and its supporting infrastructure are mature enough to be fully and reliably implemented on the road.”
To help researchers visualize how the USRP-emulated vehicles interpret information and react to messages, the team created a graphical user interface (GUI). With the GUI, users can see how the vehicles send messages to each other while they move on the road and adjust their paths accordingly.
The GUI can also be used to increase public awareness about secure V2V technology and will be displayed in an interactive exhibition at RIT’s Global Cybersecurity Institute (GCI). The new three-story facility will allow RIT to address the global cybersecurity crisis by conducting groundbreaking research, education and professional training and development.
“Our prototype uses vehicle location data exported from a commercial traffic-management simulator, so the vehicles moving around in our user interface are following realistic paths,” Twardokus said.
The GUI shows how integrating security mechanisms into the exchanges can help ensure that the information reaching the vehicles is accurate and authentic — preventing crashes and slowdowns.
“In addition to being safer on the road, people will further benefit when V2V technologies help make fully autonomous vehicles a reality instead of an ever-promised ‘coming soon’ attraction,” said Twardokus. “It would also enable vehicle platooning, which refers to groups of autonomous vehicles operating as a single unit, rather than as individuals, allowing them to operate more efficiently and at higher speeds, resulting in significant reductions in gridlock.”
While some of today’s automakers do include smart vehicle features, they often rely on sensors, which are limited to detecting objects in the vehicle’s line of sight. V2V communications is considered a complementary technology because it would allow multiple vehicles to coordinate movements without needing a direct line of sight.
The RIT project is a continuation of past capstone projects. The team is encouraging future researchers to implement anonymity measures as a privacy mechanism in their prototype and to extend it to 5G-based V2V systems.