Students showcase cyber security tools
With the swipe of a credit card or the push of a button, someone’s personal data can be stolen and used by hackers.
At the Imagine RIT: Innovation and Creativity Festival May 3, students and faculty in RIT’s Department of Computing Security will demonstrate how easily hackers can extract data from a malware-infected credit card reader. The interactive RIT Honeynet Project exhibit, located on the first floor of Golisano Hall, will also show festivalgoers how many cyber attacks RIT faces every day.
In November 2013, more than 40 million Target customers had their names, addresses, phone numbers and credit and debit card information stolen as a result of one of the largest retail data breaches to date. The Honeynet Project exhibitors will actually show festivalgoers how the malware that infected Target’s point-of-sale system worked.
“People will be able to swipe a credit card loaded with fake data into the malware-infected card reader,” said Benjamin Kelley, a fourth-year computing security student from Storrs, Conn. “You’ll then see the data be pulled off the card, sent to a commanding control server and stolen, all anonymously and in a matter of seconds.”
The exhibit will also showcase the RIT Honeynet Project, a controlled intentionally vulnerable system that allows hackers to attack it for the purpose of observing and collecting statistics on computer-based attacks against RIT. The project is part of international Honeynet Project, a nonprofit security research organization dedicated to investigating the latest attacks and developing open source security tools to improve Internet security.
“The name Honeynet comes for the fact that we are tricking attackers into thinking that we have valuable or ‘sweet’ data, when really they can’t do any harm to the fake system,” said Jared Stroud, a third-year computing security student from Pike, N.Y. “After the attack, we are able to find out where in the world they are attacking from, the exact attack vectors that they used to break in and what they tried to access and execute during the attack.”
The Honeynet visualization will show recordings of actual attacks from last winter. As thousands of IP addresses execute their malicious attacks, the visualization shows Honeynet absorbing the information and “pwning” the attacker.
“I think most people are aware that they could be vulnerable to cyber attacks,” said Kelley. “I hope that this exhibit will show people just how many there are and that we need to stay one step ahead of hackers to prevent them.”
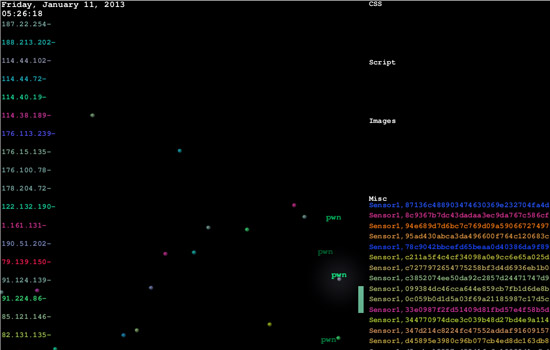 The RIT Honeynet Project is a controlled vulnerable system that allows hackers to attack it for the purpose of collecting statistics on computer-based attacks against RIT. The Honeynet visualization shows the IP addresses of attackers and the subsequent “pwning” of the attacker as their failed execution is stored.
The RIT Honeynet Project is a controlled vulnerable system that allows hackers to attack it for the purpose of collecting statistics on computer-based attacks against RIT. The Honeynet visualization shows the IP addresses of attackers and the subsequent “pwning” of the attacker as their failed execution is stored.